Security in VMware Virtual Appliances
Today I got a reminder of a post I have been meaning to write about security best practices and VMware Virtual Appliances.
A question was raised on the VMTN community VCSA - what is the default “upgrade” user for?
That is a very legitimate question!! Giving a user all rights with no password can become an issue. But in this case since it is used (most probably) for the purpose of the upgrade of the VCSA from version to version - then it might OK (or not… ).
Which leads straight into the next subject - what users (and what are their rights) exist on the vCenter Server Appliance?
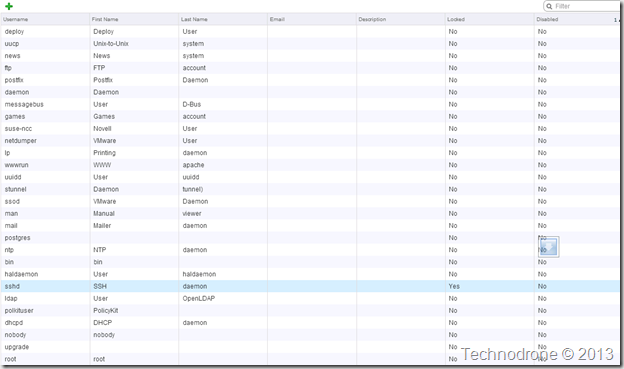
Let’s have a quick look at what users there are on the VCSA (screenshot is all the local users on my VCSA that are both not locked or disabled)
So firstly let me say that is a hell of a lot of users in the server that in essence is one of (if not the most) important part of your Virtual infrastructure.
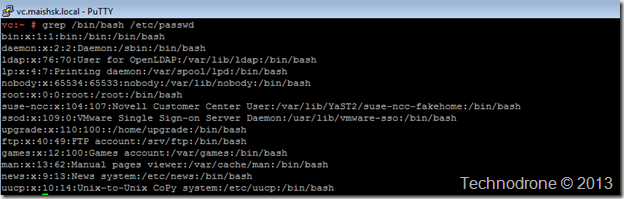
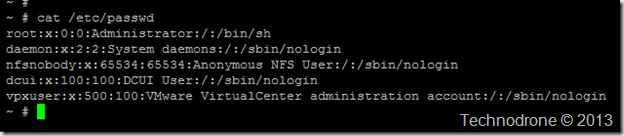
You might say (and rightfully so) that even if the users are defined - that does not mean that they can actually log into the system - for that they would need some kind of shell access. So I checked which users actually have shell access. That would be users who do not have /bin/false or /sbin/nologin in their profile. This is what I got
Let’s concentrate on some of the users in the list.
lp - Access to printer hardware; enables the user to manage print jobs.
ftp - FTP user
man - Used for man
games - Access to some game software
news - Used for news application
uucp - Serial and USB devices such as modems, handhelds, RS-232/serial ports.
For someone that values security - all our Linux boxes are hardened (as they should be), so the first thing we do is run the following:
userdel shutdown
userdel halt
userdel reboot
userdel games
userdel news
userdel gopher
userdel ftp**(Just to clarify - I do not advise running any of the above commands on your vCenter Server without proper testing and approval from VMware and doing so might void your support.
Be warned!!)
If you were to ask me - most of the users listed above have absolutely no business being on a production box… especially not on my vCenter!!!!
In VMware’s defense I should say that I checked which users were available on other VMware appliances - such as the vCOPS appliances and the new Log Insight appliance - and most of these users were not present on either of them. Perhaps this is the way going forward.
VMware have made progress - but I still do not feel 100% comfortable with the vCenter virtual appliance even after I wrote my post last year - Should You Patch the vCenter Server Virtual Appliance?
vCenter has all the keys to the kingdom - and VMware must make the utmost effort to make sure that no possibility of exploit can used by leaving silly holes and possible security vulnerabilities open in the underlying operating system.
The same way that a ESXi host is locked down - there is no reason why the vCenter server should users like games on them.
Imagine if we had Pong on our vCenter…