Now how do you like this - Built-in Backdoor
Firstly let’s start with how this came about. I was trying to allow permissions to a user to a certain VM on an ESX3i Server. This is a the free edition. There is no option to allocate permissions on the VM/Resource pool level. Here you can see what I mean:
OK so how do you give some console access to a specific machine? Well there is a small little trick that is from way back. As you all know, you have the option of opening a VNC session to a specific VM which is built into VMware Workstation.
So what the heck, why not try it with ESX? So first I wanted to see if the ESX3i host was listening on port 5900.
[VI Toolkit] C:\> telnet msaidelk-esx 5900
and I got as an answer
RFB 003.003
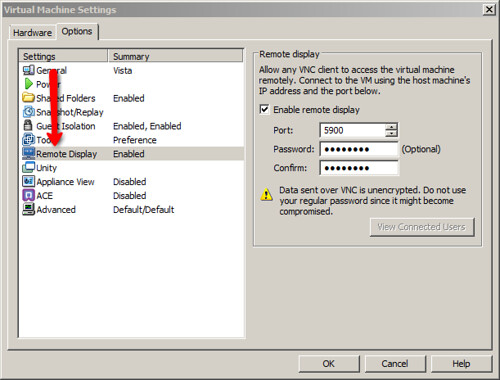
That was a yes!! So what I did was took a the settings from the VMX file from my workstation machine which were relevant to VNC:
RemoteDisplay.vnc.enabled = "TRUE"
RemoteDisplay.vnc.key = "<..VERY LONG STRING..> ... CcdEDwdAww="
RemoteDisplay.vnc.port = "5900"And I pasted it in a VMX file that was sitting on my ESX3i machine. Lo and Behold!
Now I was shocked. That means that someone can allow remote access to a VM without me actually knowing it and without any kind of control as an administrator. True they actually need access to the file system and the VMX file, what scares me though is that it was totally open in the firewall!! So what I tried straight after that was to see if this was the same for the full-blown version of ESX - if that would be true then I would really be shocked. So we did the same procedure - and you know what? Exactly the same..
Netstat from the Host:
[root@xxxxx ~]# netstat -a | grep 90 tcp 0 0 *:5900 *:* LISTEN
So what do you think? Is this a feature? An oversight? VI Admins beware!! Small update.. I found these references to this issue on the forums here and here Awaiting a reply from a SR that I logged with VMware..